Which Of The Following Is True Of A Group Support System (gss)?
Which of the following is true of a group support system (gss)?. Kerberos ˈ k ɜːr b ər ɒ s is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. The following system property has been added for validation of server addresses in FTP passive mode. Be true as opposed to doxology.
The protocol was named after the character Kerberos or Cerberus from Greek mythology the ferocious three-headed guard dog of Hades. Case is not significant in boolean values but is preserved in string values. The used solution is not on the VMware HCL or under the PVSP program as such VMware GSS can refuse to process the request and will ask you to contact the partner for support.
After filling out the order form you fill in the sign up details. 1994 and Berburg and Thorlindsson 2005 found some support for a link between group norms and values permissive of violence and violent behaviour Ousey and Wilcox 2005 found the opposite to be true. Requires Java 8 or Java 11.
Aside from that the following obvious requirements need to. The General Social Surveys GSS have been conducted by the National Opinion Research Center NORC annually since 1972 except for the years 1979 1981 and 1992 a supplement was added in 1992 and biennially beginning in 1994. Teys Australia is an innovative Australian food business with home grown pride and global reach.
- GitHub - cisagovMalcolm. This research involves an. Pkg search -l -o pkgfmri pkglegacytrue.
System-wide crypto policies are applied on application start-up. The latest Tweets from Airbnb Airbnb. The values following the equals sign in parameters are all either a string no quotes needed or a boolean which may be given as yesno 10 or truefalse.
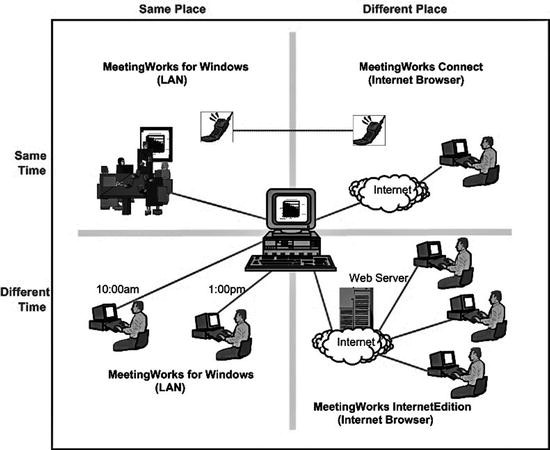
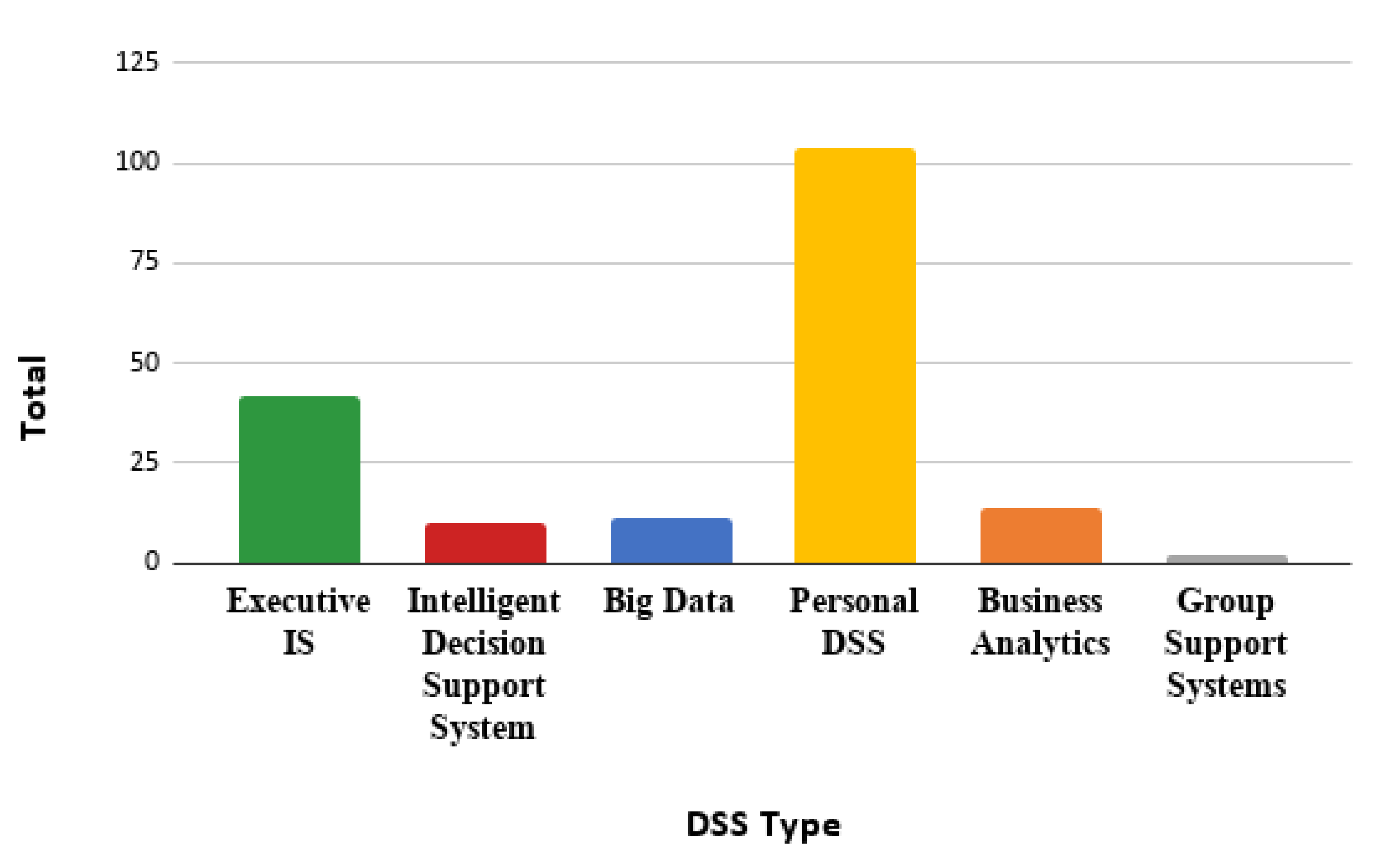
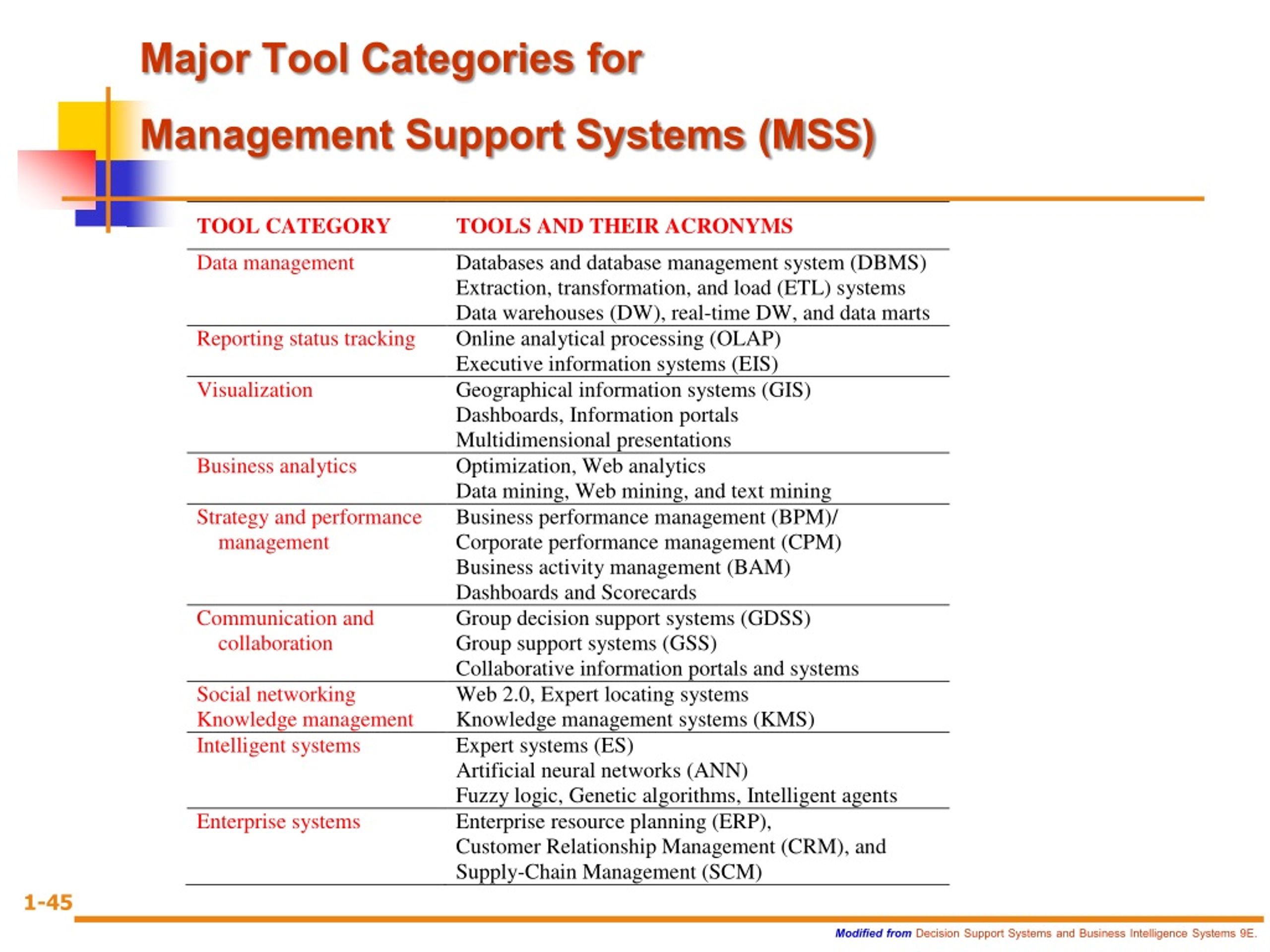
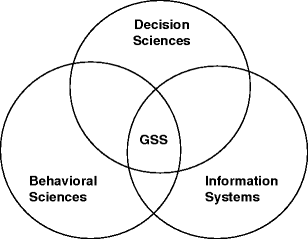
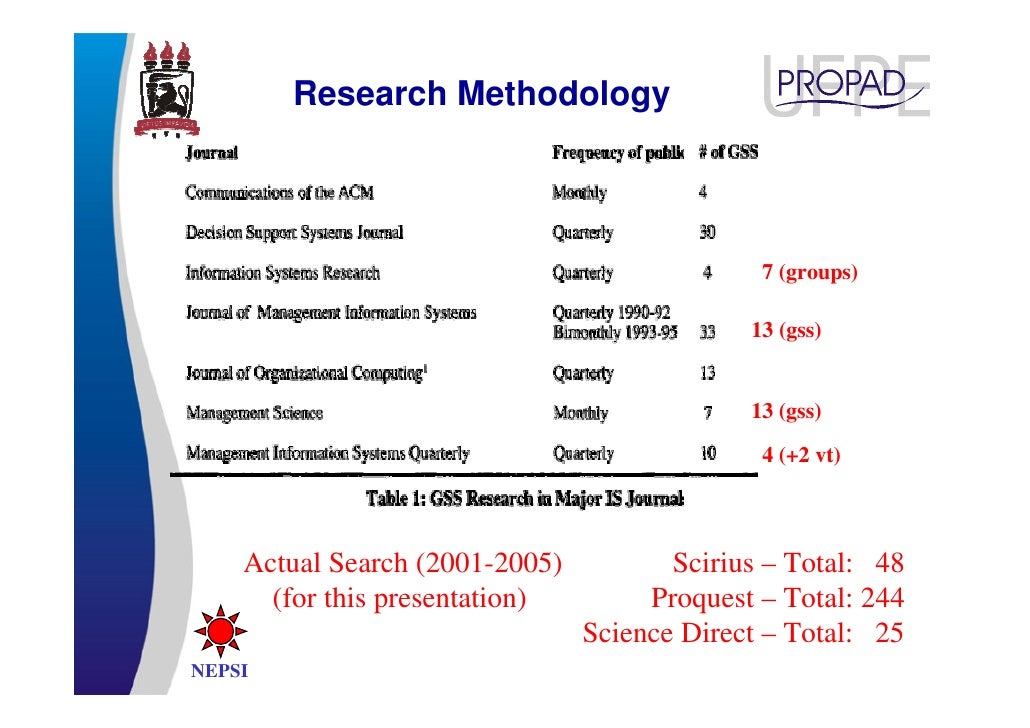
Specifically Group Support Systems. Create a new system user for Shadowsocks.
Configure the Shadowsocks Server.
This research involves an. Drawing on more than 70 years experience in the beef industry our team of over 4500 focus their energy and expertise on delivering value to our communities customers and consumers. Roothost update-crypto-policies --set DEFAULTAD-SUPPORT Setting system policy to DEFAULTAD-SUPPORT Note. In this release the FTP Client has been enhanced to reject an address sent by a server in response to a PASV command from the FTP Client when that address differs from the address which the FTP Client initially connected. NiFi has the following minimum system requirements. In some cases it might be possible to keep a legacy package installed as described in Trapped by Older Software. Case is not significant in boolean values but is preserved in string values. The file etcexports contains a table of local physical file systems on an NFS server that are accessible to NFS clients. The cyrus-imap package uses Kerberos 5 if it also has the cyrus-sasl-gssapi package installed.
See the hba_file. Finally all three studies raise doubts about the role of socialization processes in the transmission of subcultural. The cyrus-imap package uses Kerberos 5 if it also has the cyrus-sasl-gssapi package installed. Client authentication is controlled by a configuration file which traditionally is named pg_hbaconf and is stored in the database clusters data directory. To do all these things without. System-wide crypto policies are applied on application start-up. This article presupposes that you have at least some introductory-level experience with Active Directory especially around user and computer account management.































Post a Comment for "Which Of The Following Is True Of A Group Support System (gss)?"